What is Phishing?
Phishing is a method used by hackers to send emails while appearing to be from a reputable source. Their goal is to steal sensitive data. This data could be anything from login credentials to credit card information. Phishing is also used to install malware on the victim’s computer.
Top Phishing Email Subjects Globally
- HR: Vacation Policy Update
- HR: Important: Dress Code Changes
- Password Check Required Immediately
- HR: Your performance evaluation is due
- Weekly Performance Report
- LinkedIn: Who’s searching for you online?
- IT: Internet Report
- HR: Please update W4 for file
- Acknowledge Your Appraisal
- Employee Expense Reimbursement for [[email]]
In the example below you can see the display name shows Paypal.com, but the actual email address is Outlook.com.
In the example below you can see the display name shows Paypal.com, but the actual email address is Outlook.com.
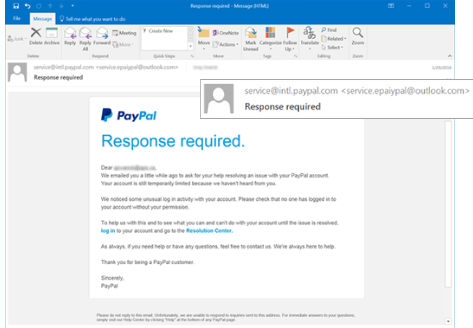
Phishing emails use several different methods to collect the data that they are after. In the example above, the blue words in the body (“log in” and “Resolution Center”) are links that the email is directing the user to click on. While the links appear to go to PayPal resources, they would act take you to fraudulent sites or download malware.
Top Attack Vector Types
- Link – Phishing Hyperlink in the Email
- Spoofs Domain – Appears to Come From the User’s Domain
- Branded – Phishing Test Link Has User’s Organizational Logo and Name
- PDF Attachment – Email Contains a PDF Attachment
- Credentials Landing Page – Phishing Link Directs User to Data Entry or Login Landing Page
Locally, we have seen Phishing emails:
- acting as employees or customers asking accounting staff to change ACH information.
- that appear to come from Microsoft or Google and prompt the user to click on and change their account information.
- that threaten the user with knowing illicit information about them and they must click on the link to make a payment, or the information would be leaked.
- appear as if it is from a company leader requesting funds transfer or to purchase gift cards.
What can be done to avoid being hooked?

DO’s and DO NOT’s
- ALWAYS check the email ‘From’ field to validate the sender. This ‘From’ address may be spoofed.
- ALWAYS report all suspicious emails to your Information Technology help desk.
- ALWAYS check for so-called ‘double-extended’ scam attachments. A text file named ‘safe.txt’ is safe, but a file called ‘safe.txt.exe’ is not.
- ALWAYS note that www.microsoft.com and www.support.microsoft.software.com are two different domains. (and only the first is real)
- DO NOT open any email attachments that end with: .exe, .scr, .bat, .com, or other executable files you do not recognize.
- DO NOT ever click embedded links in messages without hovering your mouse over them first to check the URL.
- DO NOT “unsubscribe” – it is easier to delete the e-mail than to deal with the security risks.
- DO NOT respond or reply to spam in any way. Use the delete button.
Email Security
Email security can be implemented as a first line of defense. A secure email platform such as Google WorkSpace or Microsoft 365 paired with email security and Spam control can stop most Phishing attempts.
Employee Training
As the last line of defense, our employees should have the tools and knowledge to make educated decisions to help prevent the company from falling victim to Phishing attacks. Monthly or Quarterly security training will give employees the knowledge they need to help make the right decisions when it comes time.
Twin Oaks staff has over 100 years of combined IT experience from the highest level of IT management down to the front-line warriors of Help Desk support. Whether it be multi-million dollar server environments or small business PCs and networks, Twin Oaks has the knowledge and experience to handle any IT issues your business may face. Click here for some of our key IT Services.
Sources: phishing.org, knowbe4.com

Brad Norsworthy
Senior Technology Solutions Manager

